Security is more than just a vulnerability report or a code review. Security intelligence starts with knowing your environment, then expands as you begin to track actionable data about vulnerabilities, threats, and the specifics of your environment. Making smart decisions depends on having good data at your fingertips.
No! HECTOR is much more than a security incident/event management platform. HECTOR allows you to correlate between otherwise unrelated security data points and metrics to extrapolate exactly what's happening in your environment. HECTOR allows you to see security related data that might not indicate an event or incident. Types of data include open source news feeds, vulnerability research announcements, new exploits, and data like port scans or unique host classifications.
If you thought threat intelligence was paying thousands of dollars to a security company so they could lurk in 4chan IRC channels and tell you that Anonymous is planning to hack your vertical then you've been mislead. Security intelligence applies the principles of big data to your organization allowing you to see beyond traditional analysis to make better security investment decisions.
Find out what problems are costing you the most time by reviewing you vulnerability reports over time. Are you spending time cleaning up malware infections or tracking down compromised credentials? Use actual incident data to plan your security strategy, and measure effectiveness over time.
Examine malicious traffic through your network to see what the bad guys are actually seeking to exploit. Know which ports and services are most at risk for compromise based on the malicious traffic you can see right now.
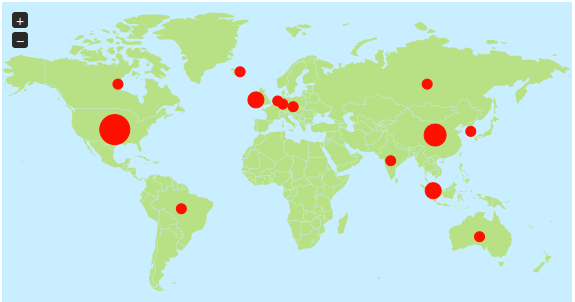
Track your attack surface. See what services and ports are available on your network and map those findings to malicious traffic and incidents.
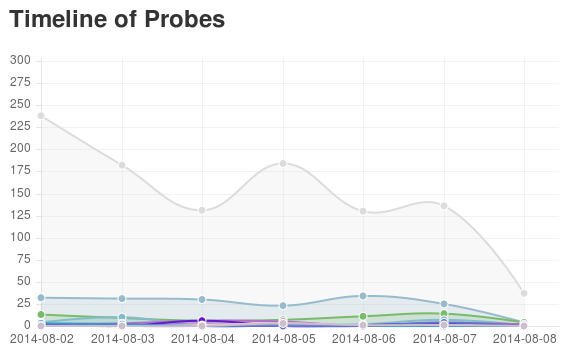
Examine vulnerability scan reports side by side with incident data and attacker behavior. Review your organizational risk profile by tracking vulnerabilities that are discovered using regular, repeatable scans.
Knowing how breaking news will affect your organization is critical to planning your security response. Understand how new vulnerabilities, discoveries, and research will actually affect your installation base to protect your customers.
Draw your own conclusions. Don't just follow the herd. Look at the landscape and chart your own course. Using HECTOR you can develop a unique profile for your environment, adapt to changes, plan for the future, measure your success and be sure that your security program makes sense!